Among the top challenges IT teams face today are the IT skills gap, digital transformation, and cybersecurity. The IT skills gap is a biggie. Not enough pros to handle today’s tech complexities.
Digital transformation? Another hurdle. Especially for businesses clinging to outdated tech and legacy systems. Rapid tech changes demand urgent management and strategy reform.
Cybersecurity is a serious risk. System vulnerability and unreliable internet connectivity compromise online security. Robust risk management strategies are a must.
1. The increasing threat of cybersecurity breaches
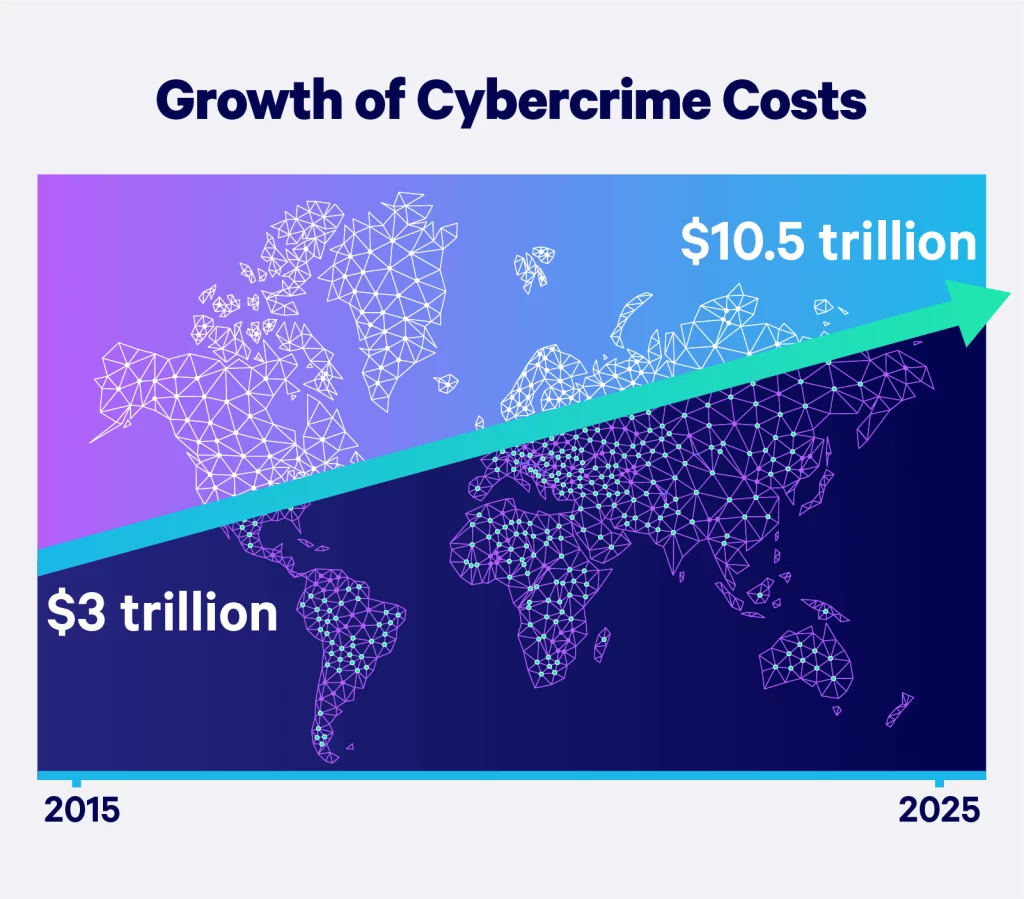
Cybersecurity is growing in complexity and importance due to digital transformation. IT management battles rapid tech advancements and a widening skills gap. Outdated tech and legacy systems? Common problems exposing vulnerabilities and risk issues.
Unreliable internet connectivity intensifies the harsh security environment. Significant threats signal a need for reinforcing IT strategy and updating tech estates.
1.1. The rise of ransomware attacks
Digital transformation has given rise to cybersecurity issues, with ransomware attacks topping the list. A critical challenge, ransomware exploits system vulnerabilities, wreaking havoc.
An effective IT strategy must prioritize robust security and update outdated tech. The skills gap complicates this endeavor. Risk management against ransomware is crucial for business continuity.
1.2. Phishing scams: A persistent threat
Digital transformation and sophisticated cyberattacks make phishing scams a persistent threat. Despite investments in managing project risk and security, the issue remains.
The skills gap makes enterprises susceptible to vulnerabilities. Phishing scams pose formidable challenges even for firms with strong IT management. Constant vigilance is needed.
2. The shift to remote work
The COVID-19 pandemic propelled a significant shift to remote work. This evolution introduced workplace challenges, emphasizing reliable IT management and strategy.
Changes exposed system vulnerabilities, risk issues, and pressure on tech estates. Outdated tech and unreliable connectivity exacerbated problems. The skills gap became evident, focusing on cybersecurity and online security.
2.1. Ensuring secure and stable remote connections
Ensuring secure and stable remote connections is a persistent challenge. System vulnerability, outdated tech, and unreliable connectivity are common problems. Investing in cybersecurity and risk management is crucial.
Addressing these issues strengthens security and covers the skills gap. IT management must adopt the latest tech while maintaining functional legacy systems. This balance establishes secure remote connections.
2.2. Managing IT support for remote teams
IT management faces challenges catering to remote teams. Unreliable connectivity, cybersecurity threats, and outdated tech hamper productivity. A robust IT strategy is crucial.
Here are some pointers:
- Adapting to the latest tech and cybersecurity practices
- Training teams to combat connectivity issues
- Ensuring system security and vulnerability are addressed
3. The need for continuous system updates
The evolving cybersecurity landscape makes continuous updates crucial. Digital transformation and security demands create a skills gap and hinder risk management. Failure to update systems leads to vulnerabilities, unreliable connectivity, and outdated tech.
Proactive IT management is needed to safeguard systems:
- Addressing vulnerabilities in unpatched systems
- Mitigating cybersecurity risks in outdated tech
- Tackling unreliable connectivity due to legacy systems
3.1. The challenge of keeping up with Microsoft updates
Keeping up with Microsoft updates is an ongoing challenge. Constant updates exacerbate the skills gap, leaving tech estates vulnerable. Outdated tech and legacy systems increase risks.
System vulnerability is a significant concern. An effective IT strategy empowers businesses to navigate digital transformation, enhancing security and reducing connectivity issues.
3.2. The importance of regular system patches
Regular system patches are key in digital transformation and cybersecurity strategy. They address vulnerabilities, outdated tech, and unreliable connectivity.
Patches assist in risk management, shielding tech estates from attacks. They resolve challenges from the skills gap. Without patches, legacy systems are prone to breaches, undermining security.
An effective IT strategy should prioritize regular patches for secure operations.
4. The demand for faster IT response times
As digital transformation accelerates across industries, the demand for faster IT response times has become a critical concern. Companies are increasingly facing common IT challenges, including system vulnerabilities, outdated technology, and unreliable internet connectivity, which collectively represent significant workplace challenges. To address these issues, organizations need to develop a proactive IT strategy that optimizes their technology infrastructure and replaces legacy systems.
Key strategies to address these challenges include:
- Developing a proactive IT strategy: This involves optimizing technology estates and systematically replacing legacy systems to reduce system vulnerabilities and enhance overall efficiency.
- Addressing the IT skills gap: A well-equipped IT team is essential for managing online security and cybersecurity, which are crucial for reducing the risks associated with system vulnerabilities.
- Implementing effective IT management practices: These practices are vital for mitigating risks and improving IT response times, ensuring that businesses remain resilient and responsive in a fast-paced digital environment.
4.1. The role of IT in minimizing business disruptions
In the digital era, the role of IT in minimizing business disruptions is more critical than ever. Companies frequently encounter workplace challenges due to unreliable internet connectivity and outdated technology. By adopting a robust IT strategy, these disruptions can be significantly reduced.
Key elements of an effective IT management plan include cybersecurity and risk management, which are essential for addressing common IT problems like system vulnerabilities and enhancing online security.
Additionally, bridging the IT skills gap is crucial for facilitating digital transformation and ensuring that the technology estates are capable of supporting modern business operations. By replacing legacy systems and improving system reliability, IT can play a pivotal role in reducing business disruptions and maintaining smooth operations.
5. The challenge of data management
Data management poses significant challenges for IT management, particularly in the face of evolving workplace demands. Managing complex technology estates, maintaining legacy systems, and addressing common IT problems such as unreliable internet connectivity and outdated technology are all part of the equation. Effective data management strategies must also consider risk management, especially when dealing with system vulnerabilities and online security.
Overcoming these challenges requires addressing the IT skills gap within organizations. Emphasizing cybersecurity is critical to protecting valuable data during the digital transformation process. As data management becomes increasingly complex, the importance of security and vulnerability management continues to grow.

5.1. The struggle with big data
The struggle with big data underscores various workplace challenges, particularly in IT management and strategy. Legacy systems, often burdened by outdated technology and system vulnerabilities, present significant risks, especially in terms of cybersecurity.
The digital transformation sweeping across industries has highlighted an IT skills gap that exacerbates common IT problems, including unreliable internet connectivity and online security concerns. Effective big data management styles need organizations to regularly update their tactics and revise their technology estates, ensuring they can handle the challenges associated with large-scale data processing and storage.
5.2. Ensuring data privacy and compliance
Ensuring data privacy and compliance is a top priority for IT management, particularly in the context of evolving workplace challenges. This involves evaluating legacy systems and outdated technology that may present system vulnerabilities and risks. A robust IT strategy is necessary to drive digital transformation, upgrade to more secure technologies, and address online security issues.
Risk management is a critical component of this strategy, encompassing:
- Identifying and addressing common IT problems: This includes dealing with unreliable internet connectivity and other technological weaknesses.
- Bridging the IT skills gap: Enhancing the organization’s ability to manage security and vulnerability effectively.
- Regular assessments of technology estates: Conducting frequent evaluations to identify potential threats and ensure compliance with data privacy regulations.
6. The pressure to adopt cloud technologies
As digital transformation becomes increasingly vital for business success, IT management faces significant pressure to adopt cloud technologies. This shift is a key component of an effective IT strategy, offering solutions to common IT problems such as system vulnerabilities and unreliable internet connectivity.
However, the transition to cloud technologies also presents challenges, including the potential widening of the IT skills gap among personnel unfamiliar with the new platforms. Additionally, migrating to the cloud demands heightened cybersecurity and risk management measures to protect against online security threats. IT management must also focus on phasing out outdated technology and legacy systems while preparing the technology estates for this critical shift.
6.1. Overcoming resistance to cloud migration
Overcoming resistance to cloud migration often involves addressing strategic IT challenges such as system vulnerabilities, cybersecurity, and reliable internet connectivity. A thorough IT strategy is essential during the digital transformation process, ensuring that technology estates are optimized for efficiency.
Risk management strategies are crucial in mitigating online security issues, updating or replacing outdated technology, and addressing the IT skills gap. Effective IT management can identify and tackle workplace challenges, making the transition to cloud technologies smoother and more successful.
6.2. Managing costs in the cloud
Managing costs in the cloud requires a comprehensive IT strategy that ensures resources are used effectively. Continuous monitoring and adjustment are vital to avoid common IT problems such as system vulnerabilities and unreliable internet connectivity.
Digital transformation often involves migrating from costly legacy systems to more efficient cloud-based models. However, this transition retains significant risk management aspects, particularly regarding cybersecurity measures to safeguard against online security risks. Successfully managing cloud costs also involves overcoming workplace challenges like the IT skills gap, necessitating training and possibly hiring outside specialists to guide the transition.
7. The need for IT budget optimization
The journey of digital transformation introduces a variety of workplace challenges, including unreliable internet connectivity, system vulnerabilities, and outdated technology. These challenges underscore the critical importance of IT budget optimization. A well-structured IT strategy can be transformative, not only addressing common IT problems but also unlocking new opportunities for growth and efficiency.
Effective IT management plays a pivotal role in identifying and closing gaps within the technology estate, particularly in dealing with legacy systems and enhancing online security. In an era where cybersecurity threats are increasingly prevalent, optimizing the IT budget is about more than just cost savings—it's about robust risk management and ensuring a secure, resilient IT infrastructure.
7.1. Balancing IT costs with business needs
Balancing IT costs with the evolving needs of the business is a complex but essential task. This balance is often challenged by workplace issues such as system vulnerabilities, where outdated technology and unreliable internet connectivity pose significant cybersecurity threats. A carefully planned IT strategy can mitigate these common IT problems, fostering a smoother digital transformation process.
Risk management must be integrated into this plan, particularly in addressing the IT skills gap. Ensuring that critical roles within the technology estate are filled with competent professionals reduces reliance on outdated legacy systems. Achieving this balance is crucial for enhancing security, mitigating vulnerabilities, and improving overall business operations.
8. The difficulty of IT talent acquisition and retention
Acquiring and retaining skilled IT talent is one of the most pressing workplace challenges in today's fast-paced digital environment. As digital transformation continues to accelerate, keeping up with the latest developments becomes increasingly difficult, exacerbating the IT skills gap. This gap poses significant risks, particularly in areas like cybersecurity and risk management.

Common IT problems such as system vulnerabilities, outdated technology, and unreliable internet connectivity further complicate the recruitment and retention of IT professionals. To address these issues, companies need to develop a robust IT strategy that directly tackles these challenges, ensuring that security vulnerabilities are managed effectively and that the organization is equipped to handle future technological demands.
8.1. The Shortage of skilled IT professionals
The shortage of skilled IT professionals is a major concern in the current digital landscape. Despite rapid advancements in technology, there remains a significant gap between the demand for IT expertise and the available talent pool. This shortage is particularly problematic as businesses increasingly rely on technology to operate, exacerbating workplace challenges such as system vulnerabilities and online security risks.
Companies are struggling with key issues like cybersecurity, risk management, and the management of technology estates, all of which are complicated by outdated technology and legacy systems. The lack of reliable IT management and strategic planning only intensifies these common IT problems, including unreliable internet connectivity and heightened security vulnerabilities.
9. The challenge of integrating new technologies
Integrating new technologies into an organization presents substantial workplace challenges. Among the most pressing are managing cybersecurity risks and developing a comprehensive IT strategy that includes a robust risk management approach. System vulnerabilities and online security become critical concerns, particularly when dealing with unreliable internet connectivity and outdated technology.
One of the common IT problems encountered during digital transformation is the difficulty of transitioning from legacy systems to newer technologies. This challenge is often compounded by an IT skills gap within existing technology estates. With effective IT management, these challenges can be navigated successfully, ensuring a smooth transition and minimizing security and vulnerability risks.
9.1. The struggle with legacy systems
Legacy systems pose significant challenges for many businesses, despite their long-standing presence within organizations. These systems often present considerable IT management issues, particularly regarding system vulnerabilities due to outdated technology. Moreover, they can significantly hinder digital transformation efforts, as they are frequently incompatible with the demands of modern IT strategies.
Common IT problems associated with legacy systems include unreliable internet connectivity, which can lead to frequent disruptions and inefficiencies in daily operations. Additionally, these outdated systems often fall short of current cybersecurity standards, increasing the risk of online security threats and necessitating heightened risk management practices.
9.2. The integration of IoT devices
The integration of IoT (Internet of Things) devices adds a new layer of complexity to IT strategy. This integration requires advanced IT management skills, particularly in addressing challenges associated with outdated technology and system vulnerabilities. IoT adoption is a key aspect of digital transformation, but it also amplifies common IT problems that teams face, such as ensuring robust cybersecurity and managing the IT skills gap.
Workplace challenges often arise from the convergence of legacy systems with new IoT devices, leading to potential threats to online security. Unreliable internet connectivity can exacerbate these issues, highlighting the need for a solid and secure IT infrastructure. The management of technology estates becomes increasingly critical as organizations work to navigate the complexities of integrating IoT devices while maintaining a focus on security and vulnerability management.
10. The need for effective IT governance
In today’s digital expanse, where every decision is a dance between risk and reward, IT governance emerges as an indispensable force. It tackles the omnipresent IT problems, weaves through cybersecurity challenges, and fortifies systems against the ever-looming threat of vulnerabilities.
But it doesn’t stop there—it’s the silent architect of IT strategies that sync seamlessly with business ambitions, bridging the chasm of IT skills gaps and wrestling with the persistent challenges of the modern workplace.
IT governance isn’t just a guide; it’s the maestro controlling the symphony of digital transformation, managing sprawling technology estates, navigating the perilous waters of legacy systems, and ensuring that every click, every connection, remains as reliable as it is secure.
10.1. The role of IT in business strategy
IT isn’t just an afterthought in business strategy—it’s the very lifeblood that pulses through the veins of an organization, addressing common IT problems and steering the ship through the stormy seas of digital transformation. It’s the bulwark against system vulnerability, the shield that ensures cybersecurity, and the relentless force tackling the evolving challenges of the workplace.
By narrowing the IT skills gap and confronting the specter of outdated technology or legacy systems head-on, IT management becomes the keystone of a resilient business strategy.
It’s not just about keeping the lights on—it’s about safeguarding every digital interaction, minimizing the risks of unreliable internet connectivity, and fortifying the foundations of robust technology estates. In this proactive approach lies the secret to driving business performance to new heights.
10.2. Ensuring IT alignment with business goals
Aligning IT with business goals isn’t just a checkbox on a to-do list—it’s the linchpin of effective IT management. It’s about crafting an IT strategy that doesn’t just sit in parallel with business objectives but intertwines with them, addressing the persistent problems like unreliable connectivity, system vulnerabilities, and the ever-present IT skills gap. It’s the strategic glue that holds together the ambitions of digital transformation.
The challenge of integrating legacy systems with cutting-edge technology isn’t just an obstacle; it’s the proving ground for maintaining updated, resilient technology estates that stand the test of time. This alignment isn’t just about reducing system vulnerability or enhancing online security—it’s about embedding cybersecurity into the very DNA of the business, ensuring that every strategic move mitigates risks and propels the organization toward its goals.






